The Importance of Security in LIMS Data Management
Over the past few years, we’ve all seen data breaches with significant operational, financial, and legal impacts on organizations, and these adverse events are only increasing.
The risks to data security are particularly onerous for labs that use outdated lab data management software or software solutions that don’t meet the strict requirements of clinical and life science organizations. These legacy softwares often haven’t kept up with cyber-security threats derailing laboratory operations.
Most labs now require a Laboratory Information Management System (LIMS) that supports robust, multi-layered security. When picking a LIMS for your laboratory, secure data management is one of the most essential features to consider. For LIMS software, nothing is more secure than Lockbox.
What does Lockbox provide to ensure LIMS Data Security?
Lockbox LIMS provides comprehensive and customizable security features to keep the data in your LIMS secure. This includes:
- Login security and user authentication tools
- User permissions and system access controls
- Vulnerability monitoring tools
- Complete audit trails
- Data encryption
How Does Lockbox Provide the Most Secure LIMS?
Lockbox is built on the Salesforce Platform and comes with all the security features Salesforce has to offer. Salesforce is a Platform as a Service (PaaS) that allows applications like Lockbox to be hosted on Salesforce’s cloud-based infrastructure.
- Salesforce’s data security controls are aligned with the United States’ National Institute of Standards and Technology (NIST) guidelines.1
- This includes access control, network security, data protection, threat detection, and incident response.
- For maintenance, compliance, and disaster recovery purposes, Salesforce enables your Lockbox instance to be served from one location with transactions replicating in near real-time across two or more separate locations.
- Salesforce also provides Transport Layer Security (TLS) technology that protects your information using both server authentication and classic encryption.2
- Unlike computer operating systems, Salesforce does not require patching. Salesforce is always up to date – no input or interaction from administrators or users is required.
If you would like to learn more about the security features provided by Salesforce contact one of our LIMS experts today!
Lockbox LIMS System-level Access – Who can access what, and when?
Log-In Security and User Authentication
The login process is particularly important because it is the first line of defense for your LIMS. Security features beyond usernames and passwords are critical to overall data quality and data security.
- Multi-factor Authentication (MFA): It is nearly impossible for phishing attackers to steal credentials and take over accounts when MFA is in place. A user must provide two pieces of evidence (factors) that validate their identity. One factor would be something they know, like their username and password, while the second could be something they have, like an authenticator app or a security key.
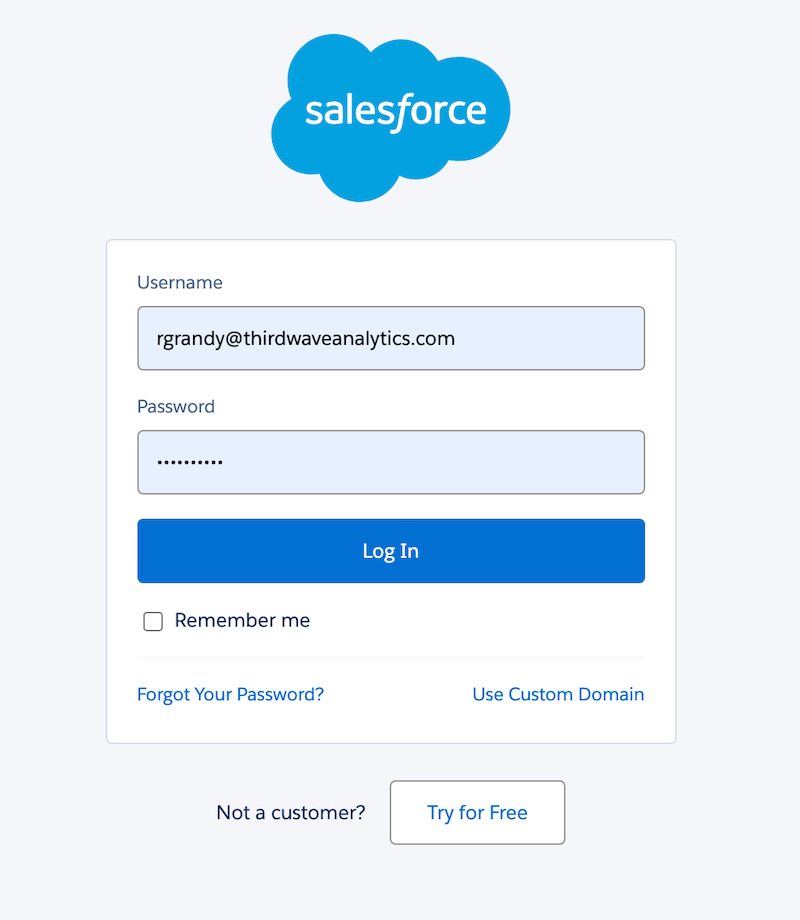
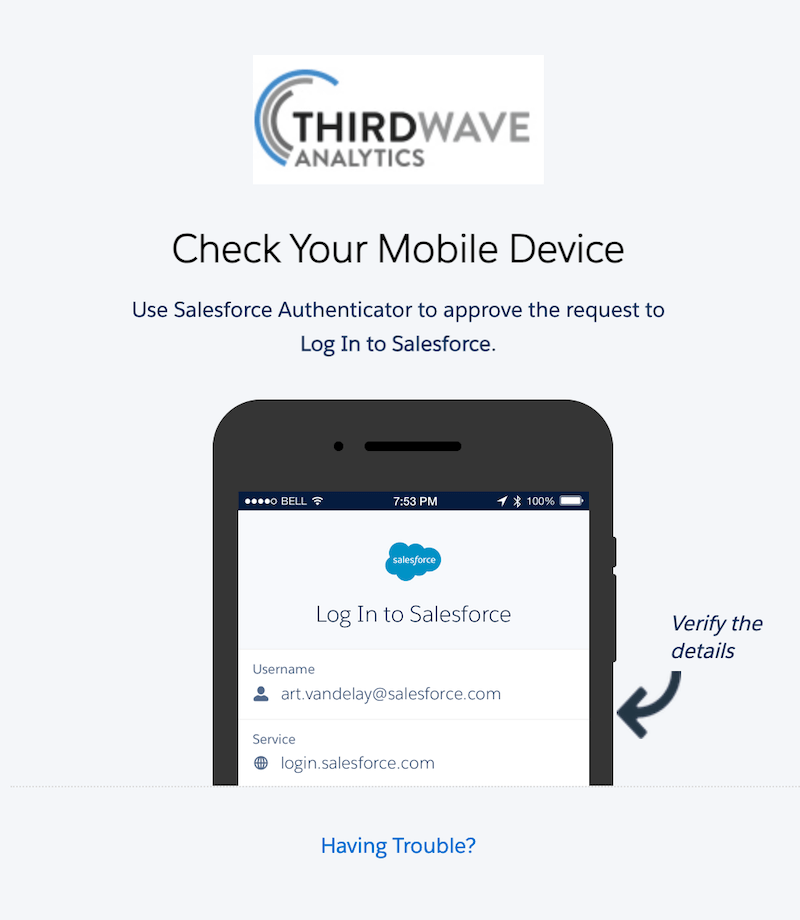
- Single Sign-On (SSO): SSO is an authentication method that enables users to access multiple applications with one login and set of credentials. For example, this feature would allow users to use their employee login credentials to login to Lockbox.
- Custom login flows: This feature guides users through a robust verification process (like asking security questions or providing extra information) before letting the user access the central database.
- Device activation: A security measure that identifies login attempts from unrecognized devices or IP addresses, requesting the user to provide extra pieces of evidence to authorize their access.
- Session security: This feature adds an extra layer of protection from unattended devices by setting an expiration timer for user sessions. Therefore, if an account sits still for X amount of time, the user will be logged out automatically.
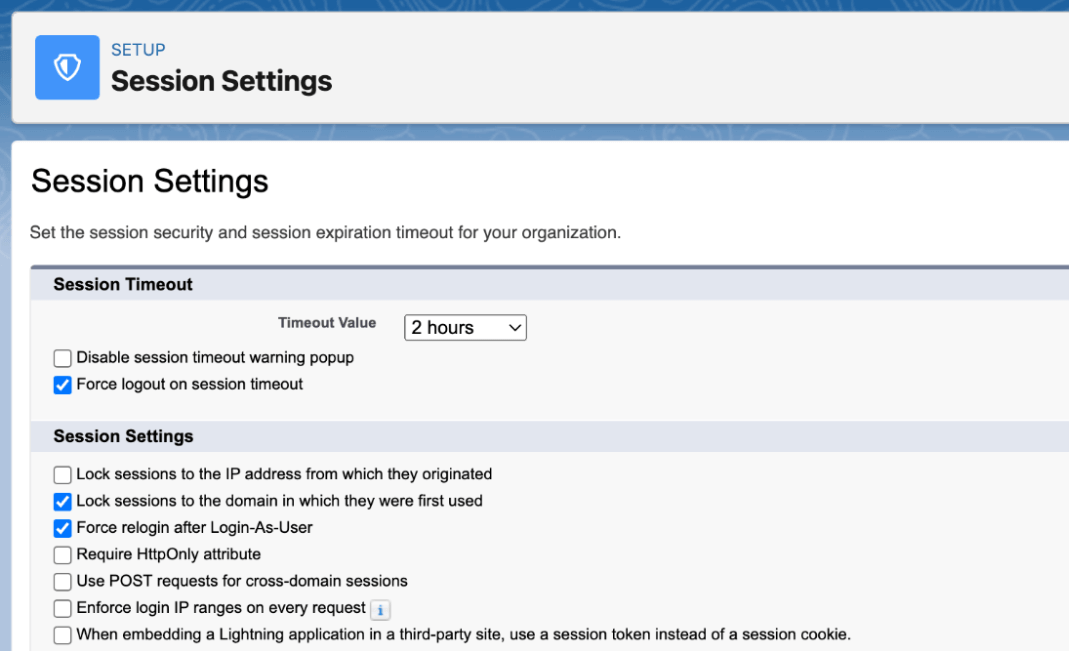
- Login from Trusted IP addresses: Lockbox can be configured to restrict the IP addresses that users can log-in from. This allows admins to set a range of trusted IP addresses (within a company’s virtual private network [VPN], for example) so any session starting outside the determined range will be blocked.
User Permissions and Data Management
Once users are inside the LIMS, the next level of security is the permissions they have, in other words, what data sets they have access to. Although you can provide universal access, this is less than optimal as it puts your data at risk. Before setting these permissions, you should identify which areas each user will need access to. This process must be a collaboration between administrators, IT professionals, and your Lockbox implementation team.
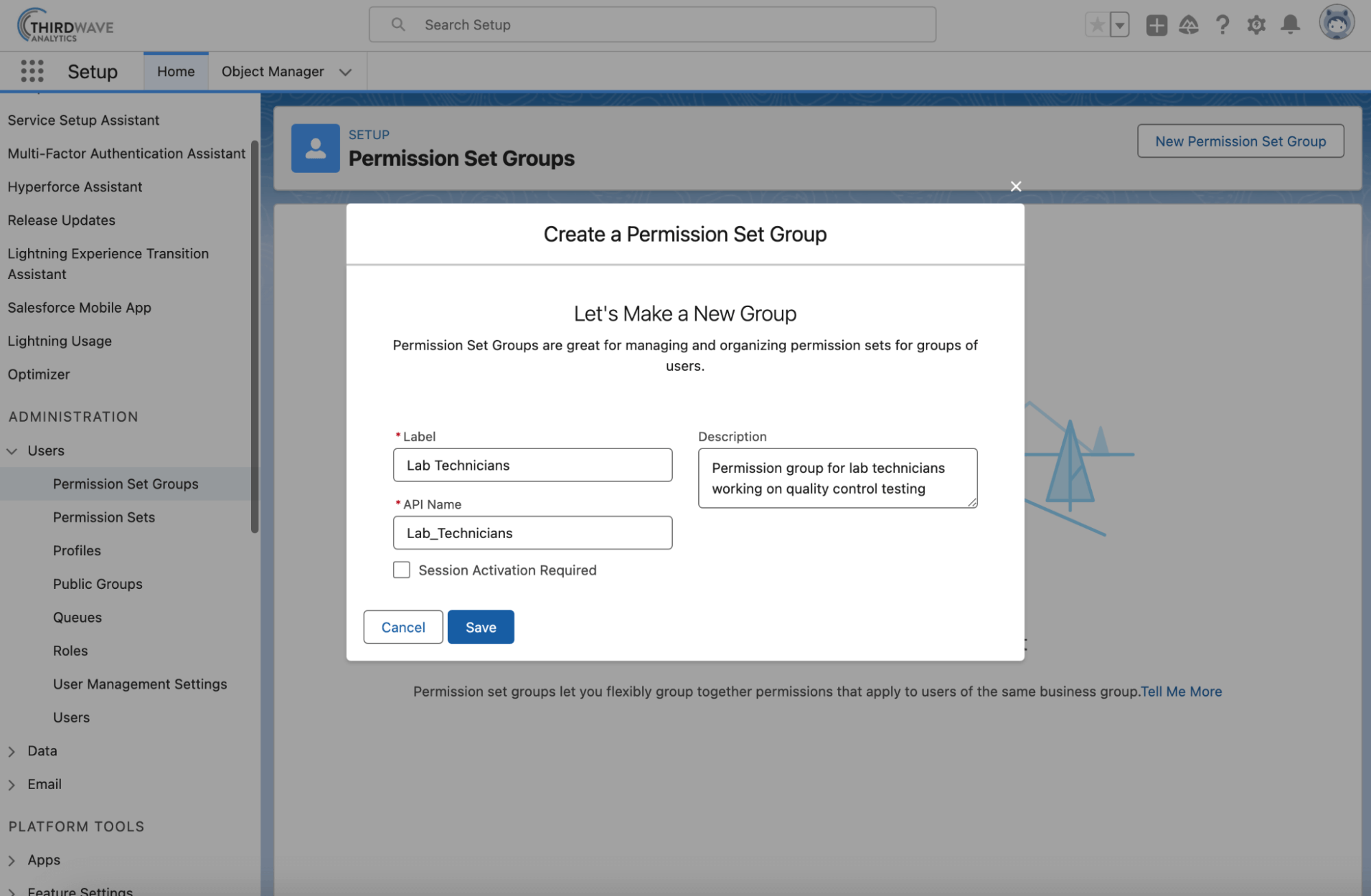
- User roles and profiles: System administrators or your implementation team can set users with specific permissions allowing you to quickly set up new users and keep better control using a hierarchical model. User profiles allow you to give a set of permissions to new users by assigning a profile to them.
- Create user groups: User groups allow permissions to be assigned to every particular user in that group. This is a great way to set permissions to specific work teams that require similar permission levels.
- Set permissions to individual users: This feature allows administrators to control what individual users can see and/or edit.
- Deactivate User Accounts: Admins are responsible for promptly removing users when they are no longer with the company. Upon an employee’s departure, the admin should immediately deactivate users so they can no longer use their Salesforce credentials. By doing so, you ensure that only authorized users are accessing your laboratory information management system.
- Customer portal: Your implementation team can create a customer portal where your lab’s customers can interact with your Lockbox instance but have significantly reduced access to objects and records. This is highly customized to meet your needs. Check out our customer portal page to learn more!
- Object and Field Permissions: Administrators can specify users’ access to create, read, edit, and delete records for each object. These permissions can also be configured at the field level which could restrict users or groups of users from viewing, editing, or creating data in individual fields.

LIMS Administrator Tools
Lockbox offers features that allow LIMS admins to identify system vulnerabilities in real time.
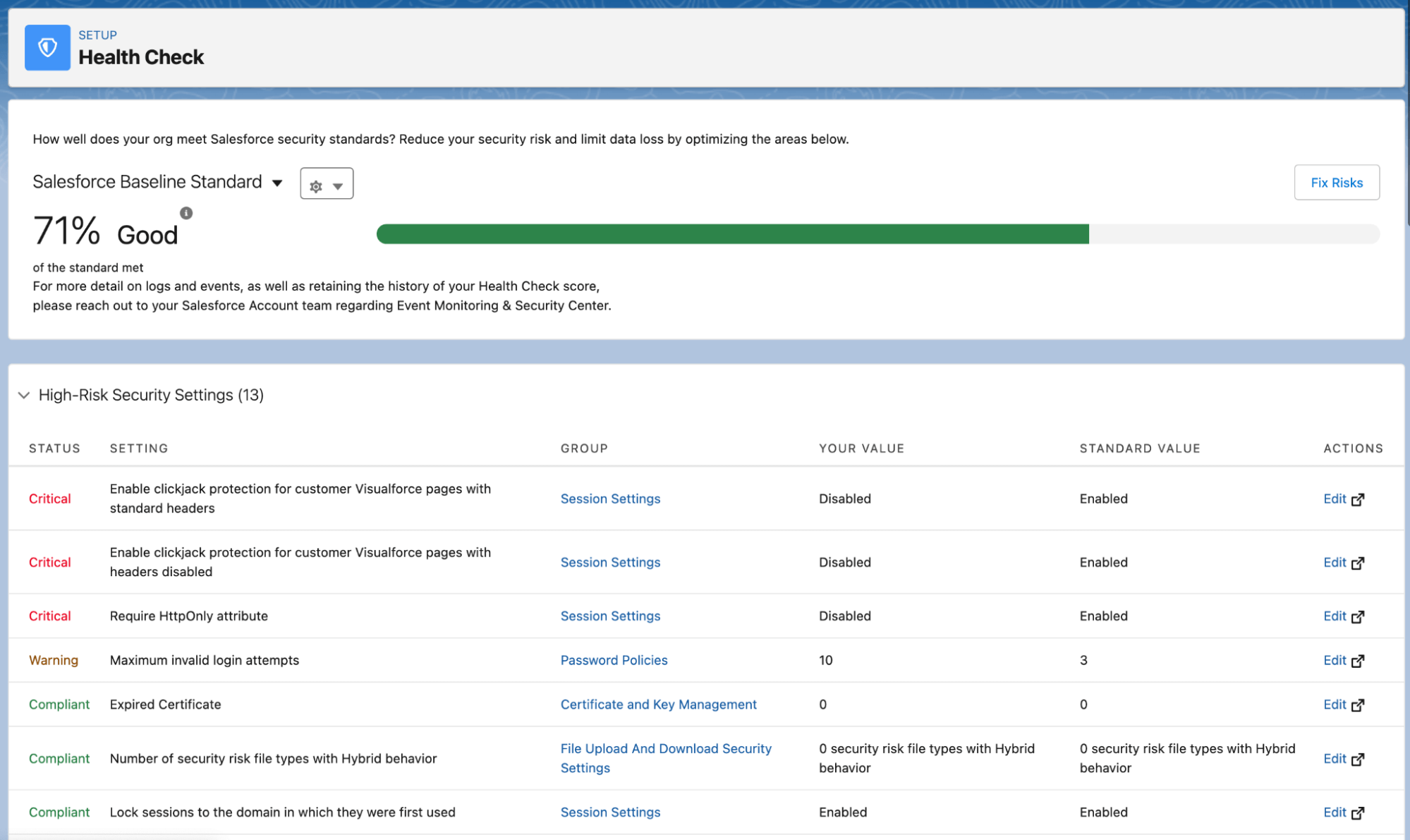
- Security health check: Administrators can utilize the Health Check feature to identify and fix vulnerabilities in their LIMS security settings. After running the Health Check administrators will receive a summary score showing how your organization measures up to the Salesforce Baseline Standard.
- Monitor Login History: Admins can monitor all login attempts for their lab’s LIMS. The Login History page shows up to 20,000 records of user logins for the past 6 months.
- Monitor Setup Changes: A Setup Audit Trail tracks administrator setup changes, which is helpful when a laboratory has multiple LIMS administrators.
How does Lockbox Ensure Data Integrity?
Laboratories often select a LIMS to ensure data integrity and traceability. Field Audit Trails and data encryption are two ways Lockbox LIMS supports this requirement.
Field Audit Trail
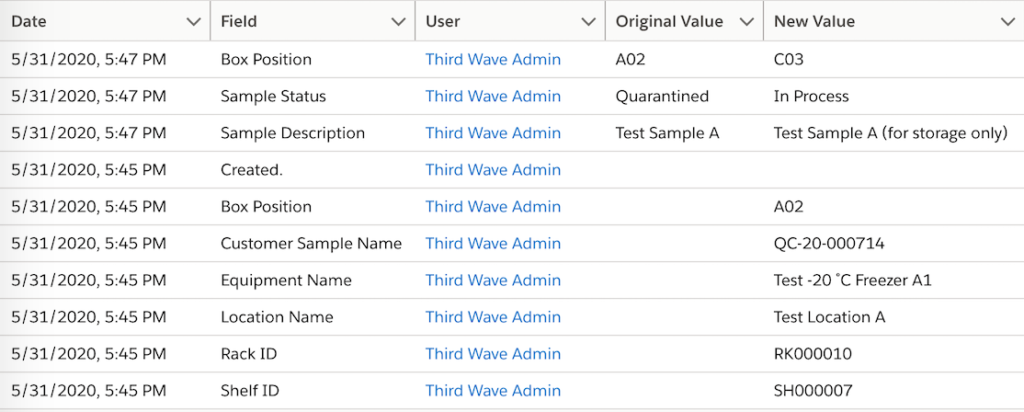
The Field Audit Trail is a critical LIMS security feature. Activating the Field Audit Trail functionality allows your lab to track and display every change in your LIMS precisely, including the exact time the change occurred.
- Field audit trails allows you to track up to 60 Fields per Object.
- You can track original and new values, when changes were made and who made them.
- The field history data is stored indefinitely, or can be deleted after a set number of years as per your organization’s archival and data retention policy.
LIMS Data Encryption
Encrypted data is readable information that turns into unreadable, random-like information and can only be decrypted by a key. When it comes to secure lab data management it’s important to be able to encrypt both the entire LIMS database and specific fields.
Stored data in Lockbox is encrypted so external viewers (or unauthorized viewers at the server level) can’t see the data. Once an authorized user logs in, the information is made available. Lockbox encryption works using a unique tenant secret you control and a master secret maintained by the platform. You can create up to 50 tenants with different keys for different data sets.
This is important because you’ll want the flexibility to set your encryption rules rather than encrypting all LIMS data. You can also control who makes changes because you don’t want anyone to change encryption policies. This entails assigning editing permissions to roles and profiles or setting it so users need a series of permissions and keys.
Salesforce Shield is an enhanced encryption option that provides an additional layer of data security. This is particularly critical to laboratories that manage sensitive and confidential healthcare and life science data.3
If your lab works with sensitive data and must meet compliance standards, see our latest analysis of the capabilities your LIMS needs to meet compliance standards.
Your Lab Data Management Solution: Is it Time for an Update?
Have more questions about Lockbox LIMS security features and laboratory data management? Check out our latest article on LIMS data integrity and traceability!
If you want to make sure your data management system and workflows are as secure and streamline as possible don’t hesitate. Request a demo, contact your Engagement Director, or reach out to our Sales Team to learn more!
Footnotes: